Self-custodial wallet Safe Wallet says that a compromised developer’s laptop was at the center of last month’s $1.4 billion hack of the crypto exchange platform Bybit.
In a new thread on the social media platform X, the firm says a joint investigation with cybersecurity firm Mandiant revealed that the hacker used a multi-pronged process to breach Bybit’s security protocols.
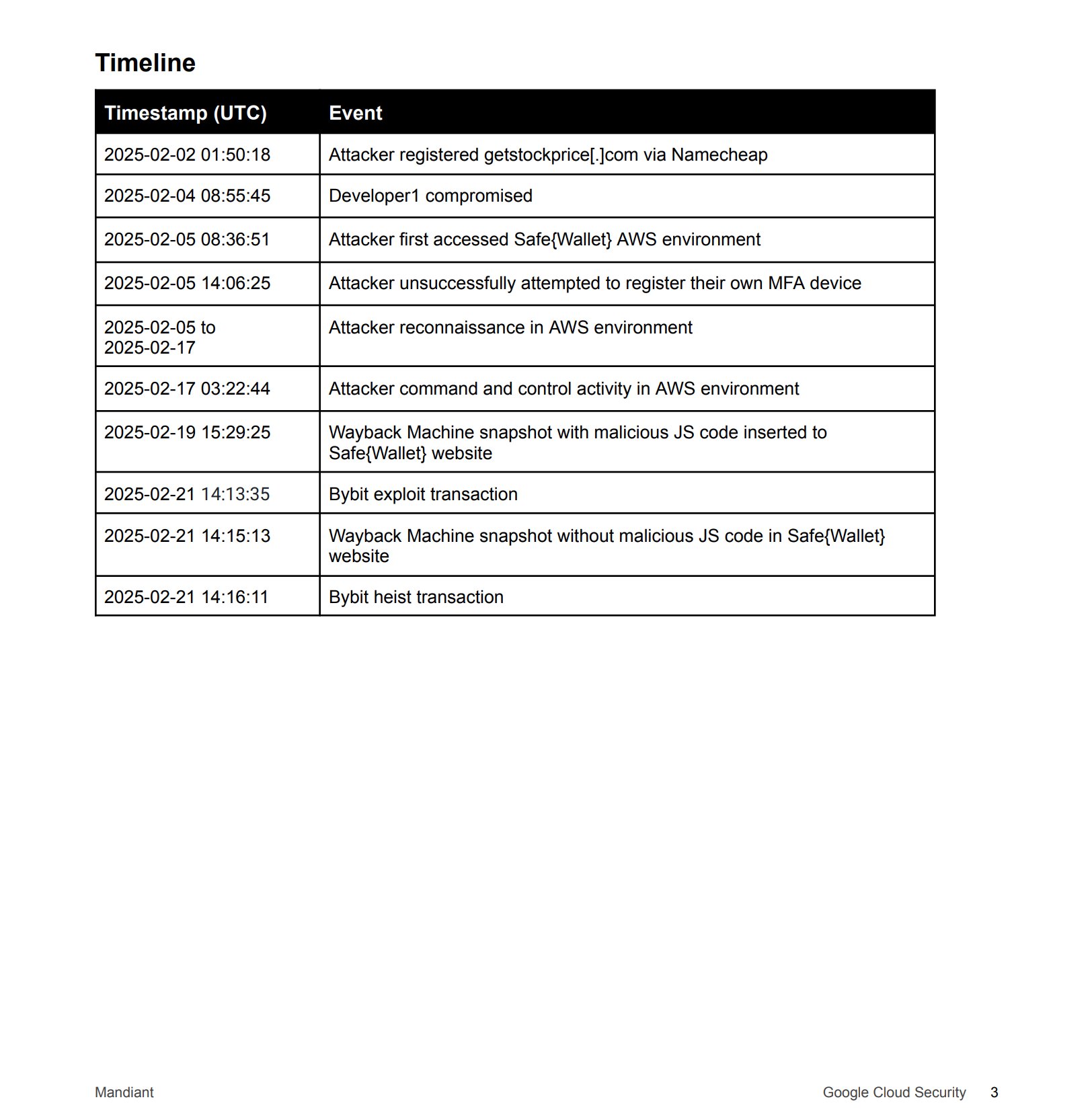
“The attack involved the compromise of a Safe Wallet developer’s laptop (Developer1) and the hijacking of AWS session tokens to bypass multi-factor authentication controls. This developer was one of the very few personnel that had higher access in order to perform their duties.”
AWS session tokens are temporary security credentials that allow users and apps to make secure API (application programming interface) calls.
Safe Wallet notes that the investigation hasn’t concluded and that further inquiry is needed to understand the hacker’s activity following the compromise of Developer1’s workstation. However, the firm says that it has bolstered its security measures beyond those of what they were before the heist.
In February, Bybit suffered a major breach linked to its Ethereum (ETH) warm wallet. At the time, data from crypto analytics firm Arkham revealed that a staggering $1.4 billion worth of ETH and Lido Staked Ethereum (stETH) were stolen, the largest crypto hack in history.
Safe Wallet says the Federal Bureau of Investigation (FBI) has connected the exploit to TraderTraitor, a hacker group associated with the Democratic People’s Republic of North Korea (DPRK).
Generated Image: Midjourney
Credit: Source link






















