According to a Check Point Research (CPR) report, users of crypto swap platform PancakeSwap, as well as crypto wallets MetaMask and Phantom, have been targeted in a phishing scam involving the theft of over US$500,000.
The crypto world is full of scammers and dangers, and in recent weeks CPR has identified multiple reports of phishing scams in which crypto wallet users have had their funds stolen while trying to install well-known wallets. The scam worked by using Google Ads to direct users to fake crypto wallets.
According to the CPR report:
Over the past weekend, CPR encountered hundreds of incidents in which crypto investors lost their money while trying to download and install well-known crypto wallets or change their currencies on crypto swap platforms like PancakeSwap or Uniswap.
Check Point Research (CPR) report
Scammers Replicate Official Websites
CPR has found that the scam has been hitting popular crypto wallets MetaMask and Phantom, with the scammers mimicking the legitimate websites almost exactly. Phantom and MetaMask wallets are the most popular wallets for both the Solana and Ethereum ecosystems.
CPR added:
CPR researchers spotted multiple phishing websites that looked like the original website because the scammers copied its design.
Check Point Research (CPR) report
For the Phantom domain, users were scammed when encountering domains such as “phanton.app” and “Phantonn.app” instead of the legitimate “phantom.app”. The same applied for MetaMask. Users encountered domains such as “MètaMask” on Google Ad campaigns.
The scam works as follows: attackers buy Google Ads in response to searches for popular crypto wallets.
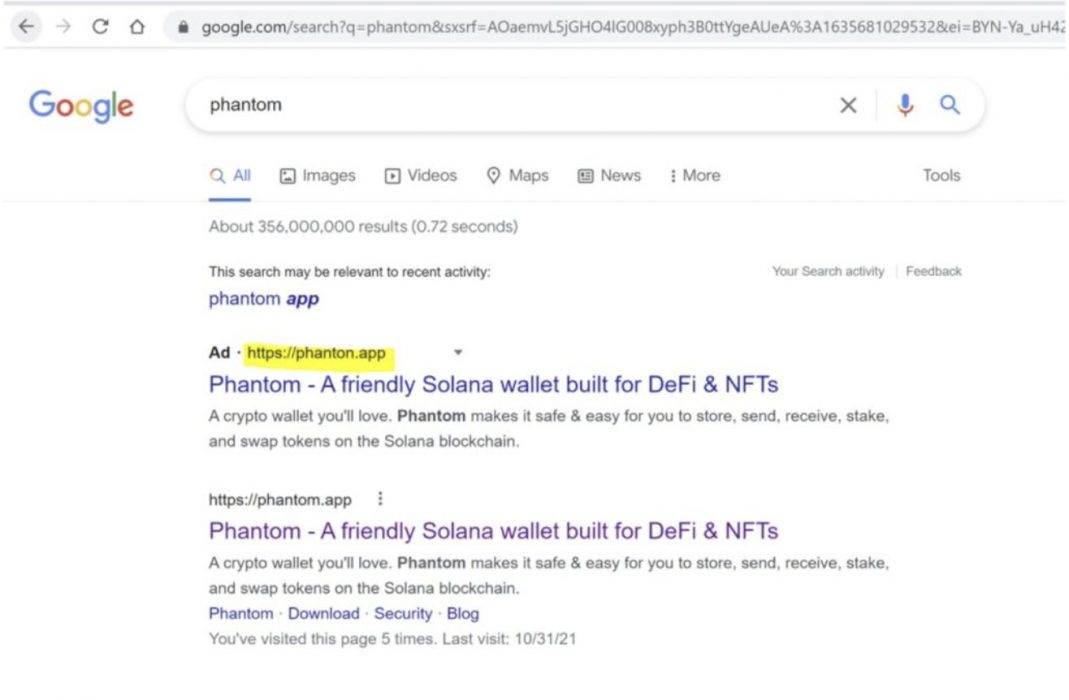
By clicking on the ad, the unsuspecting user is redirected to a phishing website, which looks almost identical to the official wallets’ website.
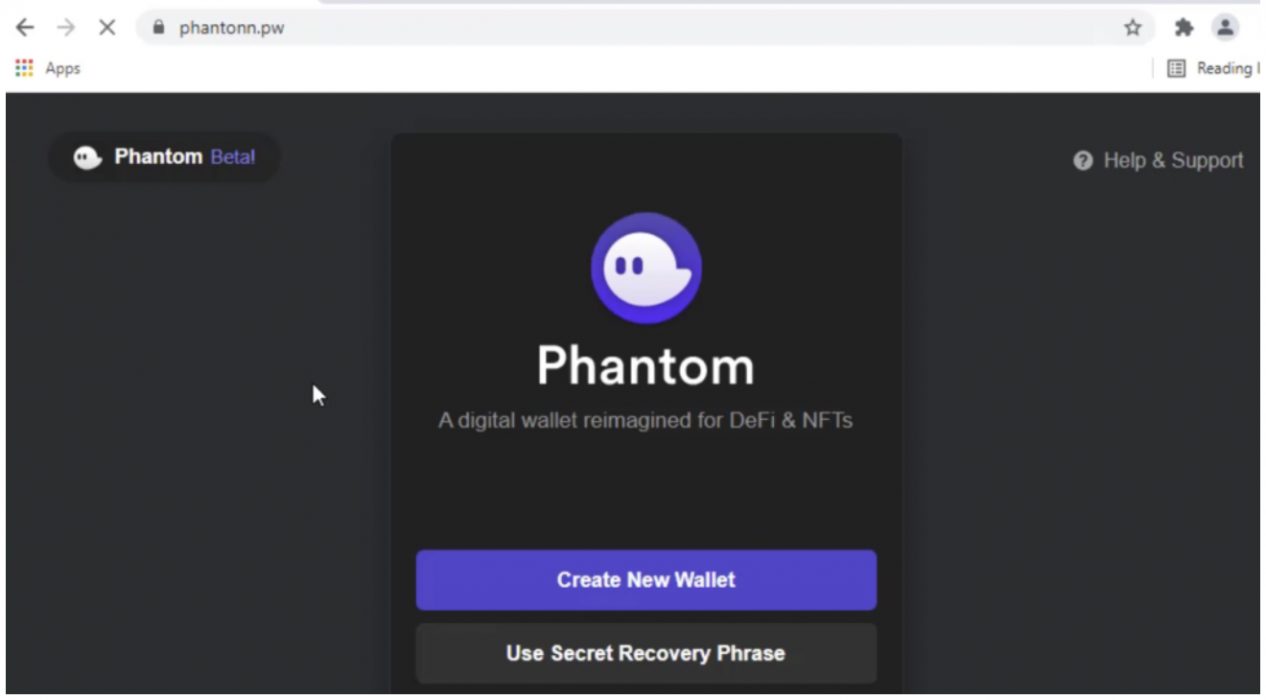
The user then clicks on the “Create New Wallet” button, which generates a message about a secret recovery phrase. Users think it is the phrase with their new wallet, though it’s actually a recovery phrase for the attacker’s website. The attacker then moves on to also steal the user’s password.
The user then clicks on “save and continue” and is redirected to the original wallet’s website. If the user then adds the chrome wallet to their browser and inserts the newly created recovery phrase, they log into the attacker’s wallet instead of creating a new one. If the user then transfers any funds, the attacker will immediately intercept them.
CPR advises crypto wallet users to “refrain from clicking on ads and only use direct, known URLs”.
Scams on the Rise
Last year, hardware wallet provider Ledger suffered an internal break of security which resulted in the exposure of 250,000 to 1,000,000 customer email addresses. Recently a number of fake Ronin wallets were spotted circulating on the Apple and Google App Stores. Fake wallets trick users into disclosing account information which then drains the funds or collectibles held within the wallets.
Disclaimer:
The content and views expressed in the articles are those of the original authors own and are not necessarily the views of Crypto News. We do actively check all our content for accuracy to help protect our readers. This article content and links to external third-parties is included for information and entertainment purposes. It is not financial advice. Please do your own research before participating.
Credit: Source link






















